
Telecast CAS System

Overview
CAS (Conditional Access System) is a key point to realize Pay-tv operation. It is a crucial factor to bring digital TV to customer successfully. There appears a paid service system among TV distributor, ISP (Internet Service Provider) and subscribers by CAS that can promote development of this industry. Telecast conditional access system is designed and developed by TELECAST independently. Its R&D is on the base of and going further from international advanced CAS. With its open, high performance, strong security system, stable site running, high-quality and timely services, Telecast CAS has won the majority recognition of operators and STB partners. Up to now, it is certificated by DVB Group ( CAS ID: 0x1EB0 CA_ System Specifier: TELECAST TECHNOLOGY CO., LTD --click it for details www.dvb.org ) and FARNCOMBE, which is the most authoritative body of CAS safety certification; and it is recognized by the famous content providers, such as HBO, DISNEY, etc. However, it is worth mentioning that Telecast CAS has been widely used for domestic and international DVB-S/S2, DVB-C and DVB-T/T2 STB manufacturers, you can always find the most suitable and cost-effective SD or HD STB for yourself.
Features
Standard:
Telecast CAS adopts DVB Simul-crypt standard and common scrambling algorithm. It can simul-crypt with any other standard CAS after testing.
Security:
The scrambling algorithm of Telecast CAS combines basic with private algorithm, 128bit key length. Four layer encryption mechanisms ensure the security of CW and keys.
Descriptison Mode:
Smart Card: The scrambling algorithm of Telecast CAS combines basic with private algorithm, 128bit key length. Four layer encryption mechanisms ensure the security of CW and keys.
CAM Card(Conditional Access Module): CAM is a single conditional access receiving module, working with digital TV stb, IRD or combo. You can select different CAM cards for various operators in different districts.
Application:
1. STB-Integrated TV: Support CAM decryption
2. IRD with CI Slot: Two 8-channel CAM cards for an IRD can decrypt 16 programs TS stream. It can be applied to independent community and hotel.
Card-less Advanced Security CAS:
Why Card-less Advanced Security CAS?
Smart cards are sold to digital TV operators. If authorization and sale of it becomes more, CA provider can hardly provide software upgrade. Much easier to be shared. Sharing can get a lot of correspondence samples between ECM and CW that provides a convenient to hackers. Once CA is cracked, operators will have to replace the smart card.
Why Card-less Advanced Security CAS?
There are two ways to get CW: One is communication process between machine and card. Second is embedding backdoors in set-top box , intercept it before CA database set the CW descrambler or simply read from the CW register and then spread out through the serial port or network. Other methods are very difficult. With the current rapid development of network technology and improved technology of set-top box manufacturing, CW sharing piracy increases more easily, set-top box design engineers can easily set backdoor to achieve this function. Since CW is public used in all set-top boxes and there is no way to dye to increase differences, so we cannot trace the source of CW. Operators and CA vendor can only do passive protection. This sharing is very common even in strictly legal protected western countries, operators are also powerless.
Functions
-Support DVB Simul-crypt Standard
-Multiple or single head-end monitor modes
-Flexible program packet separation.
-Support IC card number, post number, group team number, community number and 4 custom addressing
-Support PPC on demand by channel
-Support IPTV on demand by time or by number of times
-Support OSD display, 8 value and 4 class composite addressing
-Support mail function
-Smart card pre-opening function
-Pairing of set-top box and smart card
-Slave and master card binding/cancel binding
-Regional operation prohibition
-Conditional broadcast allows limiting and recover authorized customer to watch programs
-Subscriber recharging can activate IPPV and IPPT programs
-Support fingerprint identification function
-PIN control to reset IC card PIN code
-IC card decryption time can be controlled
-Support program recording
-Auto-send payment information, sending time, content and frequency is customized
-Independent head-end control software for program search and sync, custom program list, set-top box software
upgrade, ads image upgrade and volume adjustment
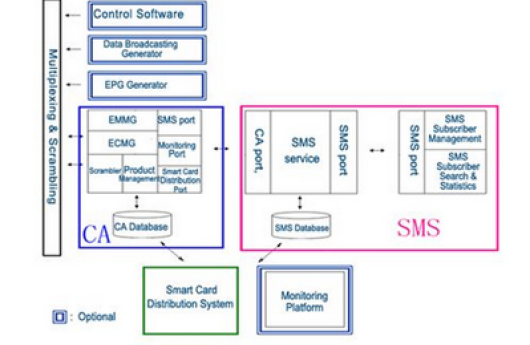
System Structure Diagram
CA Logical Structure
CA Module Function
| Module Name | Function |
|---|---|
| ECMG Module | Deliver authorized information by communicating with scrambler |
| EMMG Module | Deliver authorized information by communicating with scrambler |
| SMS Interface | Receiving authorized information from SMS module and transfer it to the format complying with Telecast CAS protocol |
| Monitoring Interface | Exchange information with monitoring platform |
| Authorization Interface | Communicate with smart card authorization module |
| PM Module | Program List and package setting |
Head-end Control Software
This software can run on application server. Multiple auxiliary functions will make up CA system. It will package private data and send it out as ASI code stream. Then set-top box will realize some special functions. Such as program management, set-top box online upgrade, boot screen, wallpaper and background image upgrade and OSD sending.
Performance and Index
-Support 256 services (Max)
-Support 128 product packets at the same time
-ECMG supports 64 TS in total
-Max support 4 different operators’ operation
-ECM bandwidth: 20 Kbps
~
28Kbps
-EMM bandwidth:
50Kbps
~
2Mbps adjustable
-Support 100 SMS connection
-Support three million users at most
-The highest priority user authorization response time is less than 30 seconds
-Max OSD byte is 1000, 20 mails at most
-1000 letters in a mail
-Support 65535 IPPV programs
-IPPT payment period and unit price is adjustable
-EMMG sending algorithm ratio is 9:3:1 by default
System Operation Security
Internet Security
Application Software Security
This software communicates between two models by TCP/IP, HTTP/HTTPS protocols.
It accesses database through inner conjunction, password can be adjusted anytime.
CA can generate private verification related to card. Illegal data adjustment cannot pass it.
Data Backup
Telecast CAS adopts database and application separation backup. The host can do image hot backup or dual hot backup even one of them is stopped.
System environment backup will arrange backup application to run instead of damaged server.
Dual hot backup ensures system switch to image server from damaged one, which can make sure server run continuously. So all user information won’t be lost.
Tape backup will copy file to tape. It adopts 8 cassettes cycle backup in general, which can reduce the loss of natural disaster like fire, flood and earthquake. Of course, you may create a backup device on hard disk. Copy files to it as backup at fixed period.
Operation Environment
Hardware
Recommended Configuration| CA / SMS Server | 1PC | 20~50 thousand users |
| SMS user device | 1PC | One set per one client |
| Application Server | 1PC | For SMS configuration by TELECAST head-end control software |
| TS broadcast card | 1PC | TELECAST Head-end and control software need it |
| Switcher(24 ports) | 1PC | 10/100M network |
Software:
-CA and Database Server
-OS: Windows 2003 Server+SP2; Windows 2008; Windows 2012
-Database: MS SQL Server2000+SP4; SQL2003; SQL2008; SQL2012
-Application: TELECAST CAS
-Application Server
-OS: Windows 2003 Server + SP2
-Application Software: TELECAST Head-end Control Software
-Others
-Anti-virus software
-ICF (Internet Connection Firewall)
Leaking Point of CW
QQ图片20161129165025.pngHow to solve it?
1. Encrypt CW communication between set-top box and smart card Take encryption measures for a communication between set-top box and smart card, do not use clear text transmission. 2. Set secure chip between set-top box and smart card Embed secure algorithm in chips. This can transfer potential safety hazard from software to hardware, chips. 3. Three ways to prevent it -Improve ECM sending frequency to share CW with a multitude of clients who can’t receive it due to slow transmission. -Position and Lock smart card. -Send unknown message to stop sharing server working 4. Share tracking measure and take legal sanctions 5. Embed decryption algorithm in set-top box instead of smart cardApplication
Multiple USB PC TV
Laptop or desktop is equipped with powerful decoding function and bigger screen. HD playing and recording can be realized. It is the best platform for receiving wireless DVB-H or DVB-T2 signal. This adopts low-cost SMD or multi-chip packing, combine a DVB-H and DVB-T2 dual model TV stick.
Mobile TV,
BUSTV, PMP
PC is not portable versus to cellphone, PMP and GPS devices. Advanced chip can form independent module and pack multi-chips. It is usually built with SPI or SDIO port, which can help general cellphone, PMP or GPS realize digital TV function.
QQ图片20161129165228.pngDVB-T2 Safety Radio
Security chip can verify signature and algorithm while CA receiving by high efficient encryption and decryption engine and powerful CPU. Then DVB-T/H/T2 will be supported by it.
Card-less CAS
To improve security and reduce cost, card-less CAS has been applied to many set-top boxes. Meanwhile, it can be used in portable devices. Use OTP storage to decrypt CW and descramble code stream.
Value-added Service
We can open valued-added service through portable devices besides DVB service. Advanced chip can help us fix account management, authorization problem. Then it will solve the problem of two-way secure communication and interaction by PC or portable devices. You can order goods by internet, VOD, information delivery, etc. Daily news, weather forecast, real-time information such as stock information, foreign exchange price and match result can be pushed on time. Meanwhile, users can pay by e-payment through account authorization and binding. Consumption record can be returned to host, then it will deduct relevant amount after client authorization verification.